Board Members Cause Cybersecurity Gaps - Why CISOs Must Protect Their Online Privacy

Cybersecurity threats now command the attention of the boardroom. And rightly so. Cyber risk oversight is a critical governance responsibility of board members. But as they wrestle with how best to improve their firm’s security posture, they ignore their own growing risk exposure.
Although they may not know it, board members are an often overlooked gap in corporate cybersecurity and are lucrative targets for bad actors seeking access to confidential and proprietary company information. When people in these roles are targeted, the impact is often of much greater significance than the actions of the average employee.
According to last year’s Verizon Data Breach Investigations Report (DBIR), board members and executives were 12 times more likely to be targeted in cyberattacks, and 71% of these cyber-attacks were financially motivated – regardless of sector.
Board members are exposed in their entangled digital lives
Companies are increasingly mindful of this and take steps to ensure that members of the boards and other executives are protected at work by a shield of security measures such as firewalls, multi-factor authentication, VPNs, and so on.
But cyber exposure goes beyond a company’s four walls. Consider the life of the average board member. They may sit on anywhere between three and five boards and travel extensively. As such they must navigate a variety of technologies and security protocols – while always remaining accessible. It’s a lot to expect of a busy board member.
So, what do they do? They use the “sneakernet” to get around the system. People are people, after all, and board members need to stay productive. They use their personal mobile device and email for communications (as a side note, the more recent 2021 Verizon DBIR found that personal and user devices are now the most breached assets). They download, review, and print documents on their home laptops. Even if they use a corporate device, they connect it to a home Wi-Fi network shared by family members and dozens of other insecure devices.
Per the Verizon DBIR, such data mishandling is now the second most common variety of privilege misuse. Furthermore, breaches that result from these cases can be difficult to detect. The discovery timeline for privilege misuse incidents can stretch from months (40%) to years (40%) showing the need for controls that can quickly catch this kind of misuse.
The data proves it
Most of us may think these assets are secure. Still, our research has uncovered revealing data about the state of personal cybersecurity and privacy of corporate executives including board members – and it’s alarming:
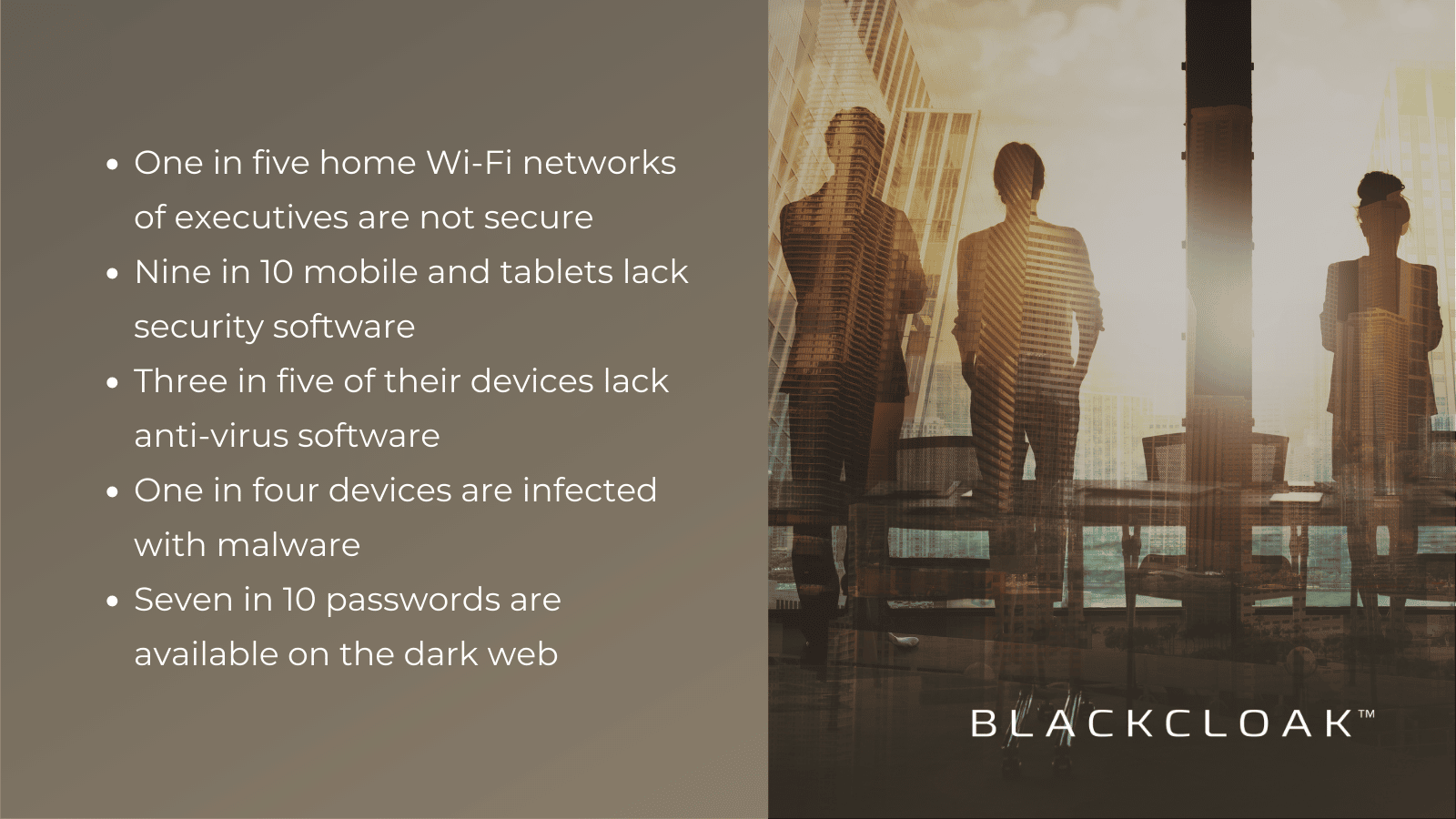
Password etiquette is also a problem. Board members use the same passwords for their personal life as they do in the corporate world. Furthermore, seven in ten write down their passwords on their little sticky notes or store them in their contacts list on the phone. Hackers can use these credentials to access other services, such as a board member’s email or other applications, and leak confidential information or gain access to corporate networks and systems – further amplifying risk.
Indeed the Verizon DBIR found that credentials are the fastest data to be compromised in any hack. It lovingly calls them “the glazed donut of data types.”
If and when a breach does occur, the company may experience losses beyond data exfiltration or a ransom. The costs per incident (which can be significant) can cause reputational damage to the organization, impact the stock price, and if you think the company’s insurance will cover the digital forensics’ legal costs and/or regulatory penalties, think again.
Who owns the problem?
This single unified digital life poses a considerable risk to board members and the companies they serve.
But who owns the problem? CISOs and CIOs should undoubtedly be concerned. But here’s the thing. But they can’t apply the same rigorous security controls that protect the corporate network and systems to a board member’s home and personal life. Board members are also statutory non-employees. Companies can’t impose onerous rules and controls that limit freedoms – and they shouldn’t want to.
Don’t fight the sneakernet; secure it
So, what are their options? They need a program that doesn’t fight the sneakernet but instead secures it. The key is partnership. Companies need to be confident that members of the board are protected in their personal lives. That their home Wi-Fi and every device connected to it are secure – including laptops, tablets, IoT, and security cameras. And they must do so without getting in the way of their productivity or privacy.
Protecting the board’s entire digital life
Cybersecurity is a boardroom issue. And board members must act in the business’s best interest to ensure their entire digital lives are protected – without feeling that the rules are being forced on them. Meanwhile, security leaders need an approach that allows them to extend the defense perimeter in a way that’s simple, seamless, and right sized for the corporate board of directors’ home environment.
To learn how this can be realized, read about BlackCloak’s services for board members in their personal lives. Or contact us to learn more about how our simple, unobtrusive, bespoke concierge cybersecurity and privacy model can protect board members as they navigate their busy lives and fiduciary duties.









