New Registration Bomb Email Attack Distracts Victims of Financial Fraud

Email bombing attacks, also known as mail bomb attacks, occur when bots flood an email address or server with hundreds to thousands of email messages. Since the late 2000s, these attacks have been a significant thorn in the sides of CISOs and ordinary email users. This nefarious act can achieve a similar outcome to that of a distributed denial of service (DDoS) attack. Email bomb spam is also frequently deployed to distract and hide important emails.
One of the most notable email bombing campaigns came in 2016. According to Brian Krebs, “unknown assailants launched a massive cyber attack aimed at flooding targeted dot-gov (.gov) email inboxes with subscription requests to thousands of email lists.” The server was so overwhelmed with email bomb spam that many .gov email addresses remained unusable for days.
Walmart ‘registration bomb’ cloaks financial fraud with inbox overload
Overview: Over the past six months, BlackCloak analysts discovered a growing number of new and existing clients whose inboxes were overwhelmed with registration confirmation emails from websites that they had never visited and had no affiliation with. Our investigation revealed these ‘registration bombs’ – the term we designated to differentiate these attacks from traditional email bombs – were deployed to distract victims from recognizing that their Walmart.com account was hacked and that financial fraud occurred.
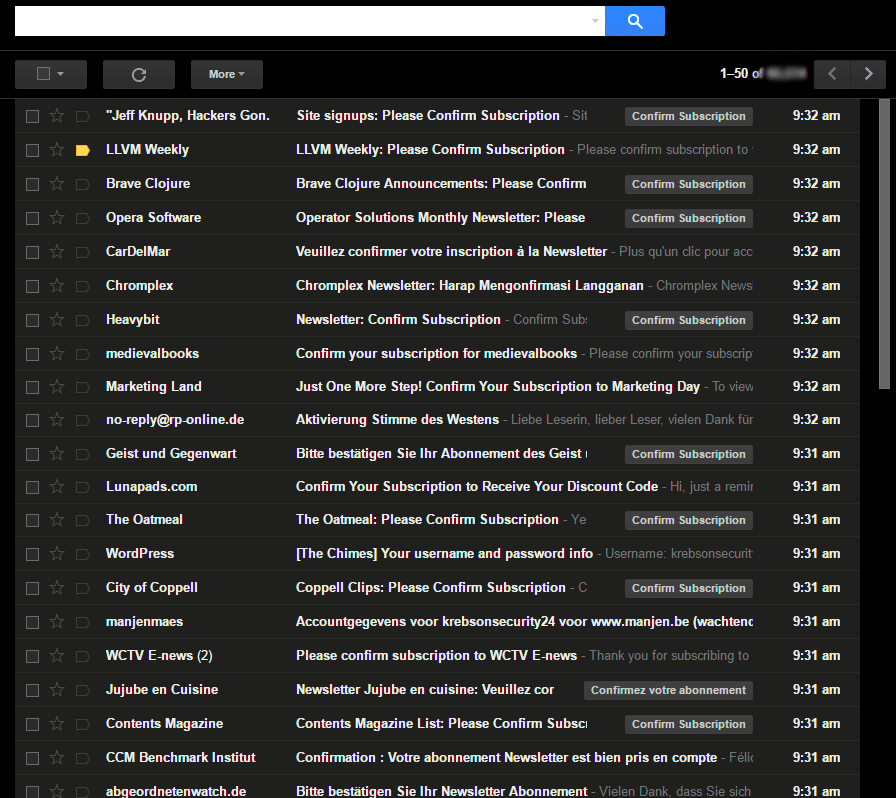
Inbox example of registration bomb courtesy of Krebs on Security
What happened: Our research found attackers obtained an unknown number of Walmart.com login credentials that were leaked onto the Dark Web, often from unrelated website data breaches. With usernames and passwords at their disposal, attackers were able to reuse these stolen credentials to log into active Walmart.com accounts, and make purchases using the valid credit card that remained on file. We quickly recognized the majority of transactions were $250 or less. This is likely intentional to avoid triggering fraud alerts. To distract from the financial fraud, the attackers overload the victims’ inbox with registration emails, ‘registration bombing’. This pushes the Walmart.com purchase confirmation email completely out of sight. Some victims received more than 500 registration emails, pushing down the purchase receipt 5, 7 and even 10 pages deep. For many, the financial fraud went unnoticed for a long period of time.
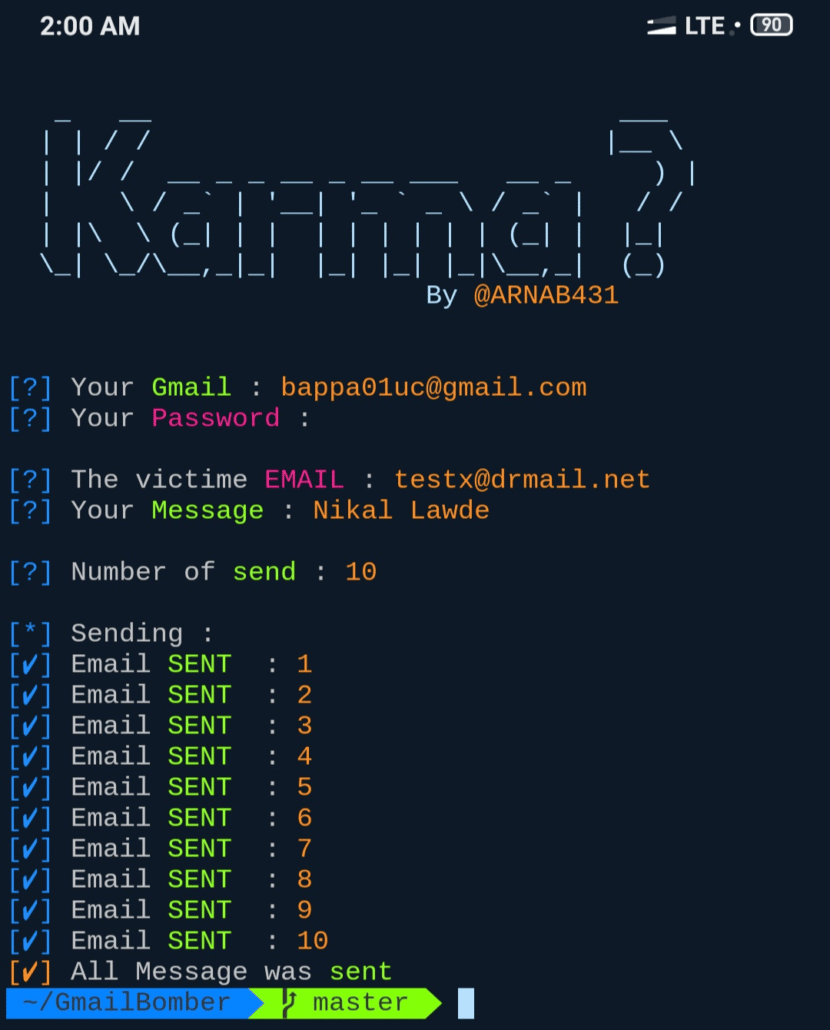
Attacker tool used to initiate attack courtesy of GitHub
What to do: It is unknown how many customers have been impacted by the Walmart ‘registration bombing’ campaign. What is clear is this is a concerted attempt by attackers to cover up the account compromise and financial fraud by drowning victims in email after email. It is important to update a password immediately. The best passwords are at least 12 characters in length, randomly generated and are not used on any other website. In addition shoppers should enable two-factor authentication and check their credit card statements for the past 6 months. Report any anomalous activity to both the retailer and the credit card company.
Reducing risk of email bombing attacks
It is easy to understand why ‘registration bombing’ is a successful tactic and a reasonable evolution of the email bomb. It’s easy to deploy and time-consuming to resolve. Moving forward, be extra cognizant of unsolicited emails. This is especially true for messages in mass quantity that are requesting an action be taken.
BlackCloak members who think they might have been impacted by the Walmart ‘registration bombing’ attack, or suspect an email bombing attack in the future should contact the Concierge Support Team immediately. And of course, don’t forget to deploy multi-factor authentication on Walmart.com and on any other e-commerce accounts that offer it.









